SSL Inspection
Secure Socket Layer (SSL) traffic, such as https://www.google.com/HTTPS, FTPs, POP3s, SMTPs, and so on, is encrypted, and cannot be inspected using Security Service profiles such as App Patrol, Web Filtering, Intrusion Prevention System (IPS), or Anti-Malware. The Zyxel Device uses SSL Inspection to decrypt SSL traffic, sends it to the Security Service engines for inspection, then encrypts traffic that passes inspection and forwards it to the destination server, such as Google.
• Use the Security Service > SSL Inspection > Profile screen (The SSL Inspection Profile Screen) to view SSL Inspection profiles. Click the Add or Edit icon in this screen to configure the CA certificate, action and log in an SSL Inspection profile.
• Use the Security Service > SSL Inspection > Exclude List screens (Exclude List Screen) to create a whitelist of destination servers to which traffic is passed through uninspected.
• Use the Security Service > SSL Inspection > Certificate Update screens (Certificate Update Screen) to update the latest certificates of servers using SSL connections to the Zyxel Device network
What You Need To Know
SSL Inspection supports the following TLS protocols and encryption algorithms
• TLS1.0 AES-CBC
• TLS1.2 AES-CBC/AES-GCM
• TLS 1.3
SSL Inspection does not support the following:
• Compression Support
• Client Authentication
Before You Begin
• If you don’t want to use the default Zyxel Device certificate, then create a new certificate in Object > Certificate > My Certificates.
• Decide what destination servers to which traffic is sent directly without inspection. This may be a matter of privacy and legality regarding inspecting an individual’s encrypted session, such as financial websites. This may vary by locale.
The SSL Inspection Profile Screen
An SSL Inspection profile is a template with pre-configured certificate, action and log.
The following table describes the fields in this screen.
label | Description |
|---|---|
General Settings | |
Server Signed Certificate Key Mode | With SSL inspection, the acts as a 'man-in-the-middle' between a client and a remote server, when the client and server are communicating using an SSL-encrypted session. Every time the client and server send data to each other, the decrypts the sender’s encrypted data, scans the plain data for threats, re-encrypts the data, and then sends the encrypted data to the receiver. • For outgoing sessions from the client to the remote server, the creates a virtual server to decrypt data and a virtual client to re-encrypt data. • For incoming sessions from the remote server to the client, the creates a virtual client to decrypt data, and a virtual server to re-encrypt data. To perform SSL Inspection for clients using SSL (HTTPS, SSH, SMTP) through the , the must check that the server’s certificate with corresponding public key are valid and were issued by a Certificate Authority (CA) listed in the Zyxel Device's list of trusted CAs. According to the selected key mode RSA 1024, RSA 2048, ECDSA-RSA-1024 or ECDSA-RSA-2048, the will construct the corresponding self-signed certificate for the virtual server. RSA is a public-key cryptosystem used for data encryption or signing messages. For data encryption, the encryption key is public and the decryption key is private. For signing messages, the signing key is private and the verification key is public. Elliptic Curve Cryptography (ECC) is a public-key cryptosystem based on elliptic curve theory, and more efficient than RSA. ECC allows smaller keys compared to RSA to provide equivalent security. For example, a 224-bit elliptic curve public key should provide comparable security to a 2048-bit RSA public key. • ECDSA-RSA-1024 indicates support for clients that support both ECDSA-256 and RSA-1024 with ECDSA-256 having higher priority, that is ECDSA-256 is used by the virtual server, if a client supports both ECDSA-256 and RSA-1024. • ECDSA-RSA-2048 indicates support for clients that support both ECDSA-256 and RSA-2048 with ECDSA-256 having higher priority, that is ECDSA-256 is used by the virtual server, if a client supports both ECDSA-256 and RSA-2048. Select a mode that the client’s browser, FTP client, or mail client supports. The will use different keys (cryptosystems) for each client according to the client’s support list. For example, if there are three clients behind a with the following key mode support: • Client 1 - RSA-1024 • Client 2 - RSA-2048 and RSA-1024 • Client 3 - ECDSA-256 and RSA-2048. If you set the key mode to ECDSA-RSA-1024, then the following will be used by each client: • Client 1 - RSA-1024 • Client 2 - RSA-1024 • Client 3 - ECDSA-256. If you set the key mode to ECDSA-RSA-2048, then the following will be used by each client: • Client 1 - sessions will not be processed (pass) by SSL inspection • Client 2 - RSA-2048 • Client 3 - ECDSA-256. |
Statistics | Enable this to have the Zyxel Device collect SSL inspection statistics. |
Profile Management | |
Add | Click Add to create a new profile. |
Edit | Select an entry and click this to be able to modify it. |
Remove | Select an entry and click this to delete it. |
References | Select an entry and click References to open a screen that shows which settings use the entry. |
Action | Click this icon to apply the entry to a policy control rule. Go to the Security Policy > Policy Control screen to check the result. |
# | This is the entry’s index number in the list. |
Name | This displays the name of the profile. |
Description | This displays the description of the profile. |
CA Certificate | This displays the CA certificate being used in this profile. |
Reference | This displays the number of times an object reference is used in a profile. |
Add/Edit SSL Inspection Profiles
The following table describes the fields in this screen.
LABEL | Description |
|---|---|
Name | This is the name of the profile. You may use 1-31 alphanumeric characters, underscores(_), or dashes (-), but the first character cannot be a number. This value is case-sensitive. These are valid, unique profile names: • MyProfile • mYProfile • Mymy12_3-4 These are invalid profile names: • 1mYProfile • My Profile • MyProfile? • Whatalongprofilename123456789012 |
Description | Enter additional information about this SSL Inspection entry. You can enter up to 60 characters (0-9a-zA-Z’()+:=?;!*#@$_%-”). The first character must be a letter. |
CA Certificate | This contains the default certificate and the certificates created in Object > Certificate > My Certificates. Choose the certificate for this profile. |
Email | Use this button to have the Zyxel Device send the selected certificate to a valid email address. Click a certificate’s row to select it and click Email to have the Zyxel Device mail that certificate. The following screen displays. 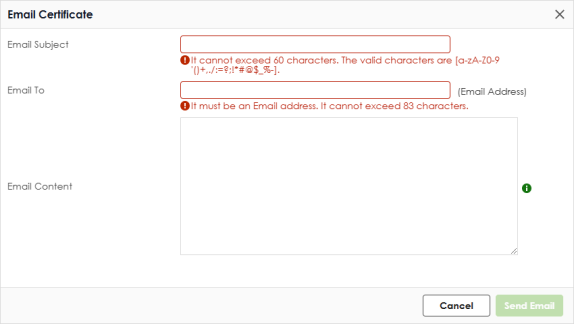 |
Email Subject | Enter a email subject text with 1-60 characters. It may consist of letters, numbers, and the following special characters: ‘()+,./:=?;!*#@$%- |
Email to | Enter up to 83 characters for the email address of the receiver |
Email Content | Enter the backup email body text using 1 to 251 single-byte characters, including 0-9a-zA-Z!”#$%&’()*+,-./:;<=>@[\]^_‘{|} and spaces are allowed. ? is not allowed. |
Cancel | Click this to send the email to the email address you configured. |
Send Email | Click this to close the screen. |
SSL/TLS version | |
Minimum Support | SSL / TLS connections using versions lower than this setting are blocked. |
Log | These are the log options for unsupported traffic that matches traffic bound to this policy: • no: Select this option to have the Zyxel Device create no log for unsupported traffic that matches traffic bound to this policy. • log: Select this option to have the Zyxel Device create a log for unsupported traffic that matches traffic bound to this policy • log alert: An alert is an emailed log for more serious events that may need more immediate attention. They also appear in red in the Log & Report > Log/Events screen. Select this option to have the Zyxel Device send an alert for unsupported traffic that matches traffic bound to this policy. |
Unsupported suit | |
Action | SSL Inspection supports these cipher suites: • DES • 3DES • AES Select to pass or block unsupported traffic (such as other cipher suites, compressed traffic, client authentication requests, and so on) that matches traffic bound to this policy here. |
Log | These are the log options for unsupported traffic that matches traffic bound to this policy: • no: Select this option to have the Zyxel Device create no log for unsupported traffic that matches traffic bound to this policy. • log: Select this option to have the Zyxel Device create a log for unsupported traffic that matches traffic bound to this policy • log alert: An alert is an emailed log for more serious events that may need more immediate attention. They also appear in red in the Log & Report > Log/Events screen. Select this option to have the Zyxel Device send an alert for unsupported traffic that matches traffic bound to this policy. |
Untrusted cert chain | |
Action | A certificate chain is a certification process that involves the following certificates between the SSL/TLS server and a client. A certificate chain will fail if one of the following certificates is not correct. • A certificate owned by a user • The certificate signed by a certification authority • A root certificate Select to pass, inspect, or block an untrusted certification chain. |
Log | These are the log options for unsupported traffic that matches traffic bound to this policy: • no: Select this option to have the Zyxel Device create no log for unsupported traffic that matches traffic bound to this policy. • log: Select this option to have the Zyxel Device create a log for unsupported traffic that matches traffic bound to this policy • log alert: An alert is an emailed log for more serious events that may need more immediate attention. They also appear in red in the Log & Report > Log/Events screen. Select this option to have the Zyxel Device send an alert for unsupported traffic that matches traffic bound to this policy. |
Apply | Click Apply to save your settings to the Zyxel Device, and return to the profile summary page. |
Reset | Click Reset to return to the profile summary page without saving any changes. |
Exclude List Screen
There may be privacy and legality issues regarding inspecting a user's encrypted session. The legal issues may vary by locale, so it's important to check with your legal department to make sure that it’s OK to intercept SSL traffic from your Zyxel Device users.
To ensure individual privacy and meet legal requirements, you can configure an exclusion list to exclude matching sessions to destination servers. This traffic is not intercepted and is passed through uninspected.
The following table describes the fields in this screen.
LABEL | Description |
|---|---|
General Settings | |
Enable Logs for Exclude List | Click this to create a log for traffic that bypasses SSL Inspection. |
Exclude List Address Settings | Use this part of the screen to create, edit, or delete items in the SSL Inspection exclusion list. |
Add | Click this to create a new entry. |
Edit | Select an entry and click this to be able to modify it. |
Remove | Select a row and click this to delete it. |
Content | SSL traffic to a server to be excluded from SSL Inspection is identified by its certificate. Identify the certificate in one of the following ways: • The Common Name (CN) of the certificate. The common name of the certificate can be created in the System > Certificate > My Certificates screen. • Type an IPv4 address. For example, type 192.168.1.35 • Type an IPv4 in CIDR notation. For example, type 192.168.1.1/24 • Type an IPv4 address range. For example, type 192.168.1.1-192.168.1.35 • Type an email address. For example, type abc@zyxel.com.tw • Type a DNS name or a common name (wildcard char: '*', escape char: '\'). Use up to 127 case-insensitive characters (0-9a-zA-Z`~!@#$%^&*()-_=+[]{}\|;:',.<>/?). ‘*’ can be used as a wildcard to match any string. Use ‘\*’ to indicate a single wildcard character. |
Apply | Click Apply to save your settings to the Zyxel Device. |
Cancel | Click Cancel to return to the profile summary page without saving any changes. |
Certificate Update Screen
Use this screen to update the latest certificates of servers using SSL connections to the Zyxel Device network.
The following table describes the fields in this screen.
LABEL | Description |
|---|---|
Certificate Information | |
Current Version | This displays the current certificate set version. |
Released Date | This field displays the date and time the current certificate set was released. |
Certificate Update | You should have Internet access and have activated SSL Inspection on the Zyxel Device at NCC. |
Update Now | Click this button to download the latest certificate set (Windows, MAC OS X, and Android) from the Zyxel cloud server and update it on the Zyxel Device. |
Auto Update | Select this to automatically have the Zyxel Device update the certificate set when a new one becomes available on the Zyxel cloud server. |
Apply | Click Apply to save your settings to the Zyxel Device. |
Cancel | Click Cancel to return to the profile summary page without saving any changes. |