Troubleshooting
This chapter offers some suggestions to solve problems you might encounter. You can also refer to the logs; see Log/Events Screens for more information.
None of the LEDs turn on.
Make sure that you have the power cord connected to the Zyxel Device and plugged in to an appropriate power source. Make sure you have the Zyxel Device turned on. Check all cable connections.
If the LEDs still do not turn on, you may have a hardware problem. In this case, you should contact your local vendor.
Cannot access the Zyxel Device from the LAN.
• Check the cable connection between the Zyxel Device and your computer or switch.
• Ping the Zyxel Device from a LAN computer. Make sure your computer’s Ethernet card is installed and functioning properly. Also make sure that its IP address is in the same subnet as the Zyxel Device’s.
• In the computer, click Start, (All) Programs, Accessories and then Command Prompt. In the Command Prompt window, type “ping” followed by the Zyxel Device’s LAN IP address (192.168.168.1 is the default) and then press [ENTER]. The Zyxel Device should reply.
If you’ve forgotten the Zyxel Device’s password, use the RESET button. Press the button in for about 7 seconds (or until the PWR/SYS LED starts to blink), then release it. It returns the Zyxel Device to the default configuration with password is 1234, LAN IP address 192.168.168.1. All configuration files, including those you saved on the Zyxel Device, will be deleted.
• If you’ve forgotten the Zyxel Device’s IP address, you can use the commands through the CONSOLE port to check it. Connect your computer to the CONSOLE port using a console cable. Your computer should have a terminal emulation communications program (such as HyperTerminal) set to VT100 terminal emulation, no parity, 8 data bits, 1 stop bit, no flow control and 115200 bps port speed.
I cannot access the Internet.
• Check the Zyxel Device’s connection to the Ethernet jack with Internet access. Make sure the Internet gateway device (such as a DSL modem) is working properly.
• Check the WAN interface's status in the Dashboard. Use the installation setup wizard again and make sure that you enter the correct settings. Use the same case as provided by your ISP.
I cannot update the IPS/application patrol/IP reputation signatures.
• Make sure your Zyxel Device has the IPS/application patrol/IP reputation service registered and that the license is not expired. Purchase a new license if the license is expired.
• Make sure your Zyxel Device is connected to the Internet.
I downloaded updated IPS/application patrol/IP reputation signatures. Why has the Zyxel Device not re-booted yet?
The Zyxel Device does not have to reboot when you upload new signatures.
My Zyxel Device is not performing the action I set in Security Service > IPS when a stream of data matches a malicious signature.
Make sure you set the Zyxel Device to Prevention mode for the Zyxel Device to take action. The Zyxel Device only creates log messages in Detection mode and does not take action.
The content filtering category service is not working.
Make sure your Zyxel Device is connected to the Internet. Use the feedback link in the screen to give feedback on a link that should or should not be in a certain content filtering category.
I configured security settings but the Zyxel Device is not applying them for certain interfaces.
Many security settings are usually applied to zones. Make sure you assign the interfaces to the appropriate zones. When you create an interface, there is no security applied on it until you assign it to a zone.
The Zyxel Device is not applying the custom policy route I configured.
The Zyxel Device checks the policy routes in the order that they are listed. So make sure that your custom policy route comes before any other routes that the traffic would also match.
The Zyxel Device is not applying the custom security policy I configured.
The Zyxel Device checks the security policies in the order that they are listed. So make sure that your custom security policy comes before any other rules that the traffic would also match.
My rules and settings that apply to a particular interface no longer work.
The interface’s IP address may have changed. To avoid this, create an IP address object based on the interface. This way the Zyxel Device automatically updates every rule or setting that uses the object whenever the interface’s IP address settings change. For example, if you change LAN1’s IP address, the Zyxel Device automatically updates the corresponding interface-based, LAN1 subnet address object.
I cannot set up a PPP interface.
You have to set up an ISP account before you can create a PPPoE or PPTP interface.
I cannot configure a particular VLAN interface on top of an Ethernet interface even though I have it configured on top of another Ethernet interface.
Each VLAN interface is created on top of only one Ethernet interface.
The Zyxel Device’s performance slowed down after I configured many new application patrol entries.
The Zyxel Device checks the ports and conditions configured in application patrol entries in the order they appear in the list. While this sequence does not affect the functionality, you might improve the performance of the Zyxel Device by putting more commonly used ports at the top of the list.
The Zyxel Device’s anti-malware scanner cleaned an infected file but now the receiver cannot use the file.
If the MD5 hash value is incorrect, then Anti-Malware removes the last packet of the file. The file is still forwarded to the receiver, but they will not be able to open it. The receiver is not notified if a file is modified by the Zyxel Device. If the file cannot be used, the receiver should contact the Zyxel Device administrator to confirm if the Zyxel Device modified the file by checking the logs.
The Zyxel Device sent an alert that a malware-infected file has been found, but the file was still forwarded to the user and could still be executed.
Make sure you enable Destroy Infected File in the Security Services > Anti-Malware screen to modify infected files before forwarding the files to the user, preventing them from being executed.
I added a file pattern in the anti-malware allow list, but the Zyxel Device still checks and modifies files that match this pattern.
Make sure you enable the anti-malware allow list. If it is already enabled, make sure that the allow list entry corresponding to this file pattern is activated.
The Zyxel Device’s performance seems slower after configuring IPS.
Depending on your network topology and traffic load, binding every packet direction to an IPS profile may affect the Zyxel Device’s performance. You may want to focus IPS scanning on certain traffic directions such as incoming traffic.
IPS is dropping traffic that matches a rule that says no action should be taken.
The Zyxel Device checks all signatures and continues searching even after a match is found. If two or more rules have conflicting actions for the same packet, then the Zyxel Device applies the more restrictive action (reject-both, reject-receiver or reject-sender, drop, none in this order). If a packet matches a rule for reject-receiver and it also matches a rule for reject-sender, then the Zyxel Device will reject-both.
The Zyxel Device’s performance seems slower after configuring DoS Prevention.
Depending on your network topology and traffic load, applying an anomaly profile to each and every packet direction may affect the Zyxel Device’s performance.
Some of the files I download don’t go through Sandbox even though it is enabled.
The Sandbox feature only applies to certain file types. Check the list in File Submission Options to see if the file types you use are included. If they are, make sure you select their corresponding check box.
Sandbox detected a malicious file, but the file still went through the Zyxel Device and is still usable.
Make sure you set your Sandbox settings to destroy malicious files in the Security Services > Sandbox: Action For Malicious File drop-down list box.
The Zyxel Device destroyed/dropped a file/email without notifying me.
Make sure you enable logs for your security features, such as in the following screens:
• Security Services > IPS
• Security Services > Anti-Malware
• Security Services > Sandbox
• Security Services > Reputation Filter
The Zyxel Device routes and applies SNAT for traffic from some interfaces but not from others.
The Zyxel Device automatically uses SNAT for traffic it routes from internal interfaces to external interfaces. For example, SNAT is used for LAN to WAN traffic. You must manually configure a policy route to add routing and SNAT settings for an interface with the Interface Type set to General. You can also configure a policy route to override the default routing and SNAT behavior for an interface with the Interface Type set to Internal or External.
I cannot get Device HA to work.
Make sure to check the following:
• Both Zyxel Devices must be the same model with the same firmware version.
• Connect the Zyxel Devices using the correct heartbeat port. This is the highest-numbered copper Ethernet ports on the Zyxel Devices - see Device HA Heartbeat Ports.
• The heartbeat port must not be in an interface that is already configured for other features.
• Enable Device HA on both Zyxel Devices.
• The management IP addresses for both the active and passive Zyxel Devices must be in the same subnet.
• SSH service in System > SSH must be enabled on both Zyxel Devices.
If you are using NCC to manage the Zyxel Device, check the following:
• Both Zyxel Devices must be registered to the same account.
• The primary Zyxel Device must be registered to a site.
• Both Zyxel Devices must be in the same organization.
You may see the following error message if Device HA fails.
• Device firmware or model mismatch detected. Check that both Zyxel Devices are the same model with the same firmware version. Update both Zyxel Devices to the latest firmware available.
You may see one of the following error messages if Device HA fails in On Cloud mode (when using NCC to manage the Zyxel Device).
After fixing the error, wait a few moments, then do the Device HA pairing process again.
• Device registration failed. Device registration fails if both Zyxel Devices are not in an organization. Go to NCC and add both Zyxel Devices to an organization.
• Devices belong to different organizations. Both Zyxel Devices must be in the same organization. Go to NCC and add both Zyxel Devices to the same organization.
• Device ownership mismatch. Check that both Zyxel Devices are registered to the same account.
• Device is not assigned to a site. The primary Zyxel Device must be registered to a site. Go to NCC, and add the primary Zyxel Device to a site.
• Internal server error. A NCC server issue occurred during the pairing process. Check that the Zyxel Device has a stable network connection to NCC. If the error persists, contact technical support with the error details.
I cannot get Dynamic DNS to work.
• You must have set up an account for Dynamic DNS service. These are supported at the time of writing. 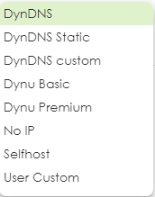

• Make sure you recorded your DDNS account’s user name, password, and domain name and have entered them properly in the Zyxel Device.
• You must have a public WAN IP address to use Dynamic DNS.
• You may need to configure the DDNS entry’s IP Address setting to Auto if the interface has a dynamic IP address or there are one or more NAT routers between the Zyxel Device and the DDNS server.
• The Zyxel Device may not determine the proper IP address if there is an HTTP proxy server between the Zyxel Device and the DDNS server.
I cannot get the application patrol to manage FTP traffic.
Make sure you have the FTP ALG enabled in Network > ALG.
The Zyxel Device keeps resetting the connection.
If an alternate gateway on the LAN has an IP address in the same subnet as the Zyxel Device’s LAN IP address, return traffic may not go through the Zyxel Device. This is called an asymmetrical or “triangle” route. This causes the Zyxel Device to reset the connection, as the connection has not been acknowledged.
You can set the Zyxel Device’s security policy to permit the use of asymmetrical route topology on the network (so it does not reset the connection) although this is not recommended since allowing asymmetrical routes may let traffic from the WAN go directly to the LAN without passing through the Zyxel Device. A better solution is to use virtual interfaces to put the Zyxel Device and the backup gateway on separate subnets. See Asymmetrical Routes and the chapter about interfaces for more information.
I cannot set up an IPSec VPN tunnel to another device.
If the IPSec tunnel does not build properly, the problem is likely a configuration error at one of the IPSec routers. Log into both Zyxel IPSec routers and check the settings in each field methodically and slowly. Make sure both the Zyxel Device and remote IPSec router have the same security settings for the VPN tunnel. It may help to display the settings for both routers side-by-side.
Here are some general suggestions. See also IPSec VPN.
• The system log can often help to identify a configuration problem.
• If you enable NAT traversal, the remote IPSec device must also have NAT traversal enabled.
• The Zyxel Device and remote IPSec router must use the same authentication method to establish the IKE SA.
• Both routers must use the same negotiation mode.
• Both routers must use the same encryption algorithm, authentication algorithm, and DH key group.
• When using pre-shared keys, the Zyxel Device and the remote IPSec router must use the same pre-shared key.
• The Zyxel Device’s local and peer ID type and content must match the remote IPSec router’s peer and local ID type and content, respectively.
• The Zyxel Device and remote IPSec router must use the same active protocol.
• The Zyxel Device and remote IPSec router must use the same encapsulation.
• The Zyxel Device and remote IPSec router must use the same SPI.
• If the sites are/were previously connected using a leased line or ISDN router, physically disconnect these devices from the network before testing your new VPN connection. The old route may have been learned by RIP and would take priority over the new VPN connection.
• To test whether or not a tunnel is working, ping from a computer at one site to a computer at the other.
Before doing so, ensure that both computers have Internet access (via the IPSec routers).
Before doing so, ensure that both computers have Internet access (via the IPSec routers).
• It is also helpful to have a way to look at the packets that are being sent and received by the Zyxel Device and remote IPSec router (for example, by using a packet sniffer).
Check the configuration for the following Zyxel Device features.
• The Zyxel Device does not put IPSec SAs in the routing table. You must create a policy route for each VPN tunnel.
• Make sure the To-Zyxel Device security policies allow IPSec VPN traffic to the Zyxel Device. IKE uses UDP port 500, AH uses IP protocol 51, and ESP uses IP protocol 50.
• The Zyxel Device supports UDP port 500 and UDP port 4500 for NAT traversal. If you enable this, make sure the To-Zyxel Device security policies allow UDP port 4500 too.
• Make sure regular security policies allow traffic between the VPN tunnel and the rest of the network. Regular security policies check packets the Zyxel Device sends before the Zyxel Device encrypts them and check packets the Zyxel Device receives after the Zyxel Device decrypts them. This depends on the zone to which you assign the VPN tunnel and the zone from which and to which traffic may be routed.
• If you set up a VPN tunnel across the Internet, make sure your ISP supports AH or ESP (whichever you are using).
• If you have the Zyxel Device and remote IPSec router use certificates to authenticate each other, You must set up the certificates for the Zyxel Device and remote IPSec router first and make sure they trust each other’s certificates. If the Zyxel Device’s certificate is self-signed, import it into the remote IPSec router. If it is signed by a CA, make sure the remote IPSec router trusts that CA. The Zyxel Device uses one of its Trusted Certificates to authenticate the remote IPSec router’s certificate. The trusted certificate can be the remote IPSec router’s self-signed certificate or that of a trusted CA that signed the remote IPSec router’s certificate.
• Multiple SAs connecting through a secure gateway must have the same negotiation mode.
The VPN connection is up but VPN traffic cannot be transmitted through the VPN tunnel.
If you have the VPN > IPSec VPN > VPN Connection screen’s Use Policy Route to control dynamic IPSec rules option enabled, check the routing policies to see if they are sending traffic elsewhere instead of through the VPN tunnels.
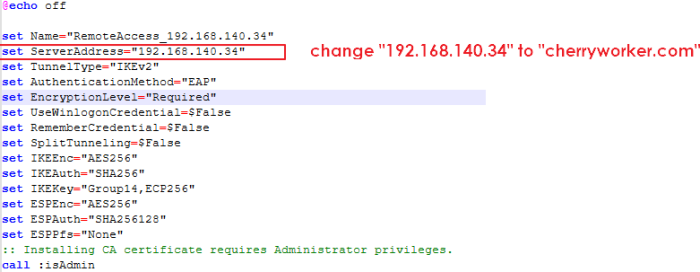
Windows 11 will not verify the certificate used in the Remote Access IPsec VPN script.
If the Remote Access IPsec VPN policy uses an interface, the ServerAddress in the downloaded Windows script will be the interface IP address. However, if the issuer of the certificate is a domain name instead of an interface IP address, then Windows 11 will not verify the certificate.
In the certificate, the issuer of the certificate is shown in the Subject field (using the domain name, cherryworker.com for example).
To fix this you must edit the downloaded script using a text editor as follows. Change the ServerAddress IP address (192.168.140.34) to the domain name used in the Subject field of the certificate as shown in the above example certificate. Save the certificate, then use it in your IPSec VPN client on your Windows 11 computer.
S
I changed the LAN IP address and can no longer access the Internet.
The Zyxel Device automatically updates address objects based on an interface’s IP address, subnet, or gateway if the interface’s IP address settings change. However, you need to manually edit any address objects for your LAN that are not based on the interface.
I configured application patrol to allow and manage access to a specific service but access is blocked.
If you want to use a service, make sure the security policy allows Security Service application patrol to go through the Zyxel Device.
My two-factor authentication is not working.
Check that match the specifications and limitation in the following list:
• Ext-users (authenticated by external servers) are not supported.
• You must setup Google Authenticator on their mobile device before you can successfully authenticate with the Zyxel Device.
I get a Google Authenticator verification error.
• Check that you enter the right verification code. The verification code should be 6 digits.
• You must enter the code within the time displayed in Google Authenticator.
• You’ve exceeded the maximum verification code failed attempts.
The schedule I configured is not being applied at the configured times.
Make sure the Zyxel Device’s current date and time are correct.
I cannot get a certificate to import into the Zyxel Device.
1 For My Certificates, you can import a certificate that matches a corresponding certification request that was generated by the Zyxel Device. You can also import a certificate in PKCS#12 format, including the certificate’s public and private keys.
2 You must remove any spaces from the certificate’s filename before you can import the certificate.
3 Any certificate that you want to import has to be in one of these file formats:
• Binary X.509: This is an ITU-T recommendation that defines the formats for X.509 certificates.
• PEM (Base-64) encoded X.509: This Privacy Enhanced Mail format uses lowercase letters, uppercase letters and numerals to convert a binary X.509 certificate into a printable form.
• Binary PKCS#7: This is a standard that defines the general syntax for data (including digital signatures) that may be encrypted. A PKCS #7 file is used to transfer a public key certificate. The private key is not included. The Zyxel Device currently allows the importation of a PKS#7 file that contains a single certificate.
• PEM (Base-64) encoded PKCS#7: This Privacy Enhanced Mail (PEM) format uses lowercase letters, uppercase letters and numerals to convert a binary PKCS#7 certificate into a printable form.
• Binary PKCS#12: This is a format for transferring public key and private key certificates.The private key in a PKCS #12 file is within a password-encrypted envelope. The file’s password is not connected to your certificate’s public or private passwords. Exporting a PKCS #12 file creates this and you must provide it to decrypt the contents when you import the file into the Zyxel Device.
I cannot access the Zyxel Device from a computer connected to the Internet.
Check the service control rules and to-Zyxel Device security policies.
The Zyxel Device’s traffic throughput rate decreased after I started collecting traffic statistics.
Data collection may decrease the Zyxel Device’s traffic throughput rate.
I can only see newer logs. Older logs are missing.
When a log reaches the maximum number of log messages, new log messages automatically overwrite existing log messages, starting with the oldest existing log message first.
I cannot get the firmware uploaded using the commands.
The Web Configurator is the recommended method for uploading firmware. You only need to use the command line interface if you need to recover the firmware. See the CLI Reference Guide for how to determine if you need to recover the firmware and how to recover it.
My packet capture captured less than I wanted or failed.
The packet capture screen’s File Size sets a maximum size limit for the total combined size of all the capture files on the Zyxel Device, including any existing capture files and any new capture files you generate. If you have existing capture files you may need to set this size larger or delete existing capture files.
The Zyxel Device stops the capture and generates the capture file when either the capture files reach the File Size or the time period specified in the Duration field expires.
My earlier packet capture files are missing.
New capture files overwrite existing files of the same name. Change the File Suffix field’s setting to avoid this.
My Zyxel Device CPU usage is too high. I see an alert log that says “abnormal TCP flag attack detected”.
Your FTP server is in active mode. It is sending too much traffic to the Zyxel Device. Set your FTP server to passive mode.
I cannot apply a configuration file.
The configuration file you upload to the Zyxel Device must meet the following requirements:
• The configuration file size cannot be 0.
• The configuration file must be a text file, a JSON file or a XML file.
• The model name in the configuration file must be the same as the Zyxel Device model you’re uploading to.
• Use Test to check the configuration file for errors before applying it to the Zyxel Device.
My Zyxel Device cannot assign correct IP addresses to DHCP clients in my LAN and DMZ.
Make sure your Zyxel Device is the only device with DHCP server enabled in your network.
The clients’ information I collected using Device Insight is not correct.
Make sure your clients are in the same IP subnet in the LAN/VLAN/DMZ networks behind the Zyxel Device. Information from clients that are in different IP subnets in the LAN/VLAN/DMZ networks might not be collected correctly.
To report on clients that are wrongly identified, go to Network Status > Device Insight > Feedback.
I cannot remove a client in Network Status > Device Insight.
Clients that are blocked cannot be removed. Please make sure to unblock the client you want to remove first.
My USB storage device is not compatible with the Zyxel Device.
The Zyxel Device supports USB file systems FAT16, FAT32, EXT3, and EXT4. To change the file system of your USB storage device by formatting it, follow these steps:
1 Insert your USB storage device into the computer. Be sure to back up your files before formatting your USB storage device.
2 Open File Explorer, right-click on the USB storage device and select Format.
3 In the Format window, select the desired file system:
FAT16 supports Windows, macOS, and Linux. Can store files up to 2 GB.
FAT32 supports Windows, macOS, and Linux. Can store files up to 4 GB.
EXT3 supports Linux. Can store files up to 2 TB.
EXT4 supports Linux. Can store files up to 16 TB.
4 Click Start to begin the formatting process.
Reserved System Ports
The Zyxel Device reserves the following system ports.
TCP Ports | UDP Ports |
|---|---|
53 | 53 |
179 | 67 |
830 | 68 |
953 | 500 |
2601 | 546 |
2602 | 547 |
2603 | 1812 |
2604 | 1813 |
2605 | 3799 |
2616 | 4500 |
5432 | 5246 |
7681 | 5247 |
7682 | 18121 |
Resetting the Zyxel Device
If you cannot access the Zyxel Device by any method, try restarting it by turning the power off and then on again. If you still cannot access the Zyxel Device by any method or you forget the administrator password(s), you will need to reset the Zyxel Device to its factory-default settings.
Use the following procedure to reset the Zyxel Device to its factory-default settings. This overwrites the settings in the startup-config.conf file with the settings in the system-default.conf file. It is recommended you regularly save configuration changes to your computer.
Using the R ESET Button
1 Make sure the PWR/SYS LED is on and not blinking.
2 Press the RESET button and hold it until the PWR/SYS LED begins to blink. (This usually takes about 7 seconds.)
3 Release the RESET button, and wait for the Zyxel Device to restart.
You should be able to access the Zyxel Device using the default settings.
Using CLI
If the RESET button is not working, use a terminal emulation program to reset your Zyxel Device:
1 Connect the console port of Zyxel Device to your computer using a console cable.
2 Open a Terminal Emulation program, such as Tera Term. Click Setup > Serial port, set the Speed to 115200, and click New setting to save the changes.
3 Press the REBOOT button and hold it until the PWR/SYS LED begins to blink. (This usually takes about 5 seconds.)
4 When the following text appears in the terminal emulation program, press any key within 3 seconds to enter debug mode.
BootModule Version: V1.1.5 Oct 11 2024 02:52:20 DRAM: Size = 8192 Mbytes Press any key to enter debug mode within 3 seconds. |
5 You will see Enter Debug mode in the terminal emulation program, indicating the Zyxel Device is now in debug mode. Type atkz -b and press Enter to reset the Zyxel Device to the factory defaults.
6 Type atgo and press Enter to restart the Zyxel Device. All configurations on the Zyxel Device are now reset to the factory defaults.
USG FLEX 500H> atkz -b -b OK USG FLEX 500H> atgo Booting… RAM test …… done! |
Restarting the Zyxel Device
You may want to restart the Zyxel Device when experiencing network connectivity issues. If you want to use the standby firmware as the running firmware, then select the standby firmware and restart.
Use one of the following procedures to restart the Zyxel Device.
Using the REBOOT Button
Use a pin to press and hold the REBOOT button on the Zyxel Device until the PWR/SYS LED starts blinking.
Using the Web Configurator
Go to the Maintenance > Reboot/Shutdown screen and click the Reboot button to restart the Zyxel Device.
Using CLI
Use a terminal emulation program, such as Tera Term, to restart your Zyxel Device.
1 Connect the console port of Zyxel Device to your computer using a console cable.
2 Open a terminal emulation program. Click Setup > Serial port, set the Speed to 115200, and click New setting to save the changes.
3 Log in first. Type the command copy running startup to save the current configurations as the startup configurations.
4 Type cmd reboot force and press Enter to restart the Zyxel Device.
Getting More Troubleshooting Help
Go to support.zyxel.com to find other information on the Zyxel Device.